Key Points
There's a gap in how most organizations track vulnerabilities. While defenders wait for CVEs to appear in the National Vulnerability Database (NVD), attackers are already exploiting weaknesses that have been publicly disclosed elsewhere. Commonly referred to as "Ghost CVEs" - vulnerabilities that are real, documented, but invisible to most security teams.
The NVD Delay Problem
The National Vulnerability Database is one of the most widely relied-upon sources for vulnerability intelligence. But here's the problem: NVD isn’t the first link in the chain.
When a vulnerability is disclosed, there's typically a delay before it appears in NVD. Sometimes it's minutes. Sometimes it's hours. Sometimes it's days. The reasons vary - whether it’s CVE Numbering Authorities (CNAs) taking their time to properly document the issue, or delays within NVD’s process of vulnerability enrichment. Technically, there has to be some delay, because information needs to be publicly available before NVD can publish a CVE entry.
But from a defender's perspective, those delays can increase risk. Every hour that passes between public disclosure and NVD publication is an hour where attackers have information that you don't.
Enter Ghost CVEs
The concept is brilliantly simple: track CVE identifiers that appear in public places like GitHub commits, security advisories, and mailing lists before they show up in NVD.
There's an excellent open-source project doing exactly this: GhostCVEs by RogoLabs. At the time of writing, this repository has only 14 stars on GitHub. We think it's time the security community gave this project the recognition it deserves.
Real-World Impact
This isn't just theoretical. We use Ghost CVEs as part of our Rapid Response process, and it's made a measurable difference.
Case in point: This morning, we identified CVE-2026-24512 affecting a component in our own stack.
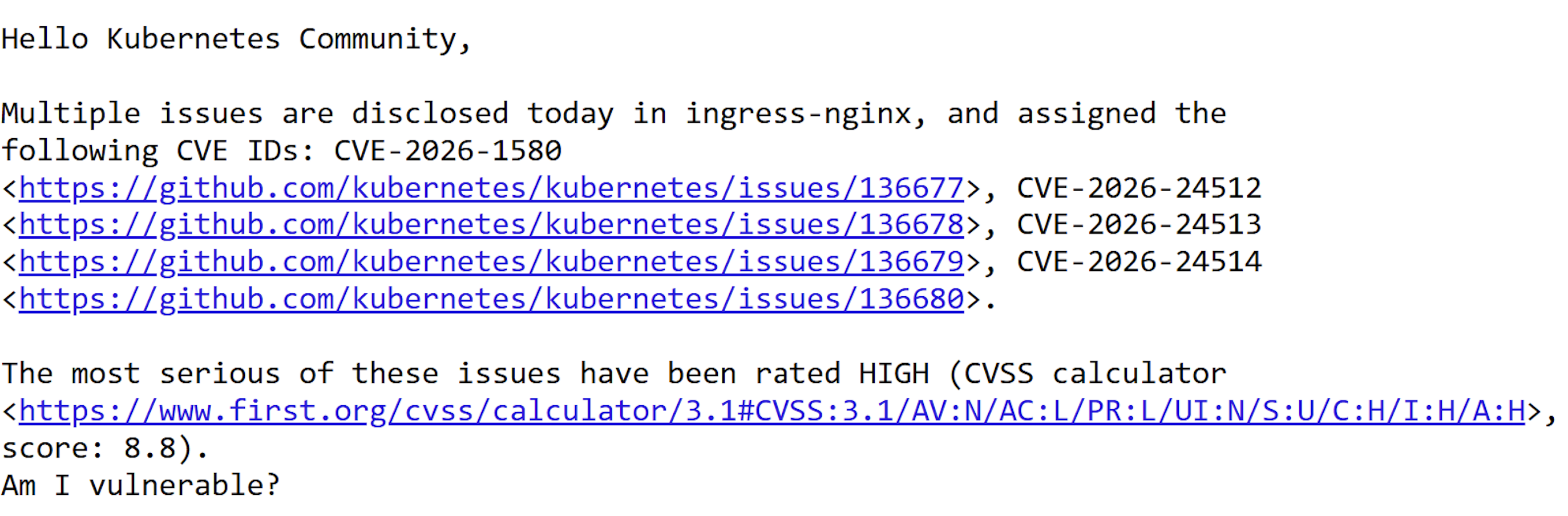
The vulnerability hadn't hit NVD yet. Most of the security community wasn't even talking about it. But because we're tracking Ghost CVEs, we saw it early and patched within 24 hours of the initial disclosure.
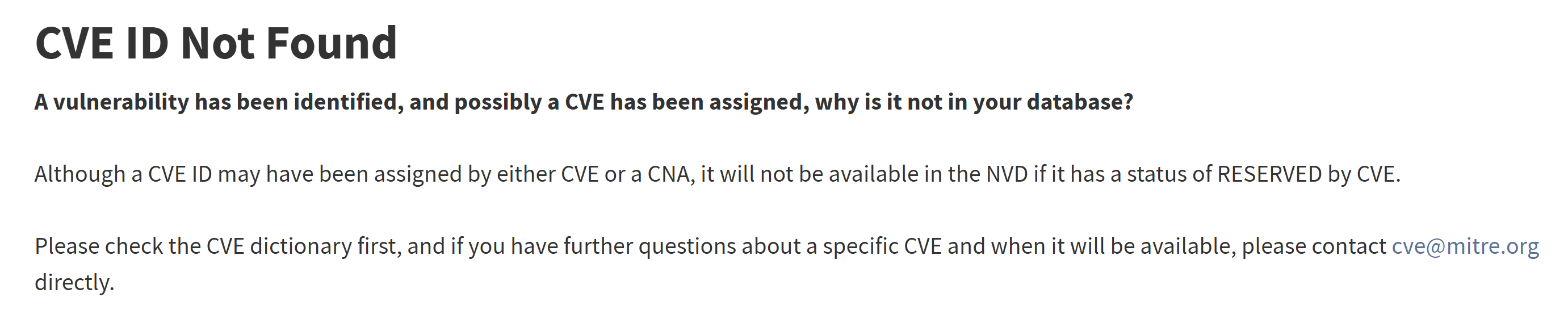
Why This Matters
Speed matters in security. The window between vulnerability disclosure and active exploitation is shrinking. Attackers are watching the same public repositories and security channels where these vulnerabilities first surface.
By integrating Ghost CVEs into our Rapid Response workflow, we're closing that gap. When a new vulnerability is disclosed - even before it's formally catalogued - we can identify affected systems, assess risk, and push protective measures to our customers faster than traditional vulnerability management approaches allow.
If you're only watching NVD, you're watching a lagging indicator. Ghost CVEs help you watch the leading edge - where the information first becomes public, where attackers are already looking, and where you need to be if you want to stay ahead.






