Meet compliance requirements without the effort
Compliance can be painful but Intruder makes the vulnerability management part easy so you can focus on what matters - security.
Security compliance, simplified.
Start scanning in minutes
Easily add targets with a URL, IP address or by integrating your cloud systems.

Audit ready reports at your fingertips
Share reports with customers, stakeholders and auditors with a click. Use analytics to demonstrate progress over time.

Flexible scanning to meet requirements
Schedule regular scans to meet compliance or business requirements. Choose how thoroughly you want to scan based on business priorities.

Automate compliance with integrations
Set up scans to automatically send evidence to Drata and Vanta. Integration Intruder with your tech stack for deep compliance automation.

Can I use Intruder for?
No matter the compliance framework, Intruder has you covered.
SOC 2 proves you can protect your customer data. Conducted annually as an independent audit, you need to continuously monitor your system for weaknesses to maintain certification.
Simplify the complexity, cost and time it takes to get certified with the gold standard of information management.
With strict vulnerability management requirements, Intruder can help reach your PCI goals faster.
Streamline healthcare compliance with expert guidance, automation and third-party attestation.
“...incredibly reliable and effective”
“It’s hard to demonstrate compliance. Intruder provides me with an effective tool to show clients and internal stakeholders that we are safe and compliant with current threats and standards.”
Trusted by 1000s of businesses worldwide
Don’t believe us? Take a look for yourself.
Simplify. Automate. Improve.
Intruder provides audit ready reports in minutes while helping you automate your vulnerability management process so you can get your compliance tasks done easily.
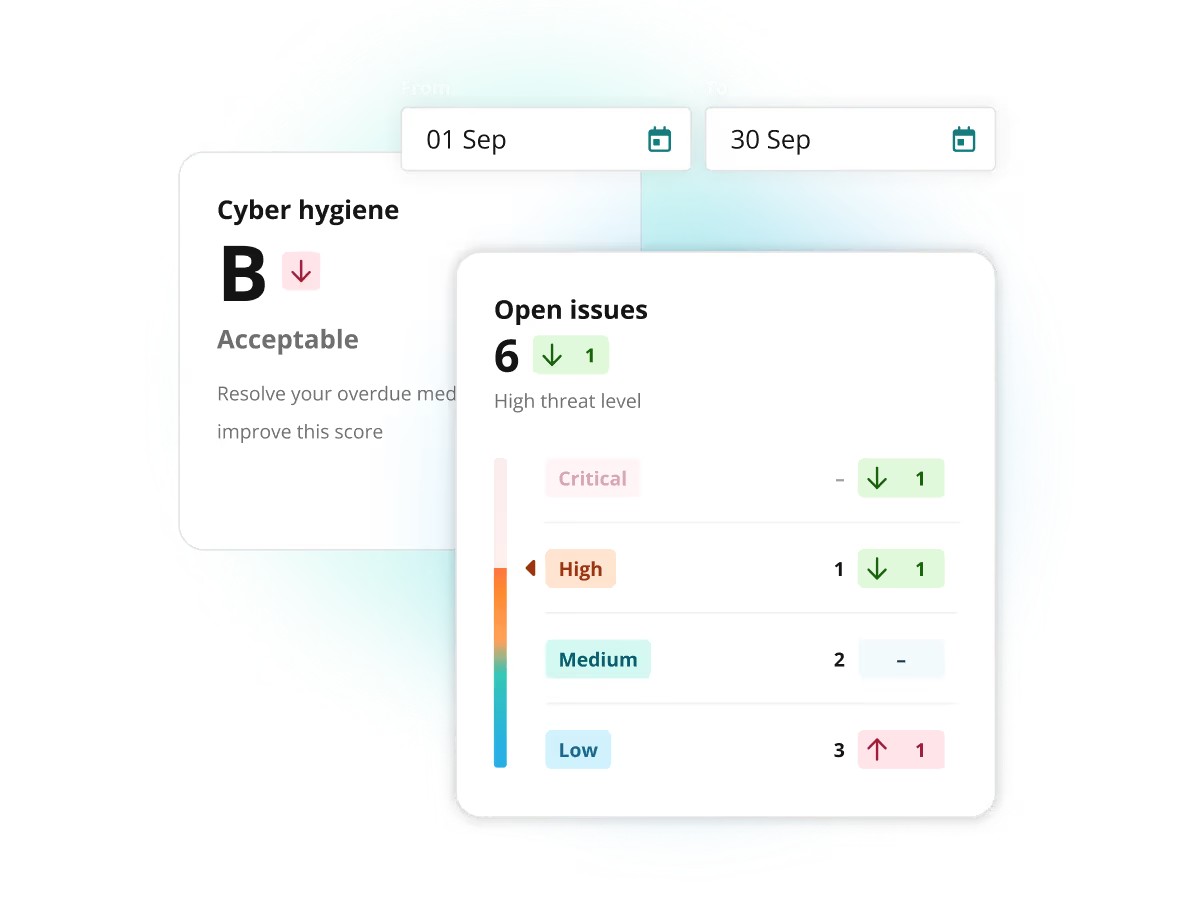
Always on. Always audit ready.
Download reports anytime that include a high level summary as well as any technical detail required to satisfy customers, stakeholders and auditors. You can access your latest scan directly from the dashboard, or filter down to specific targets or dates on the reports tab.
Simplify your compliance process
Use our API and integration options to automate compliance reporting. Intruder’s cyber hygiene score helps you track progress over time giving you a snapshot of overall health, time to fix over six months, and average time to fix issues overall.


Spend less time on compliance
Set up and start scanning in minutes, easily adding targets with a URL, IP address or by integrating your cloud accounts. Then, schedule scans to run automatically so you don’t have to think about it.
A guardian for your cloud accounts
For businesses with everything in the cloud, or those spinning up VMs and containers regularly, it is challenging to keep on top of all your systems that could be exposed to the internet.
Intruder gives you complete visibility of your cloud assets in one place, helping you maintain compliance across your whole estate effortlessly.

SOC 2 compliance: an essential guide
Simplify the complex and tedious process of becoming SOC 2 certified with our essential guide.















